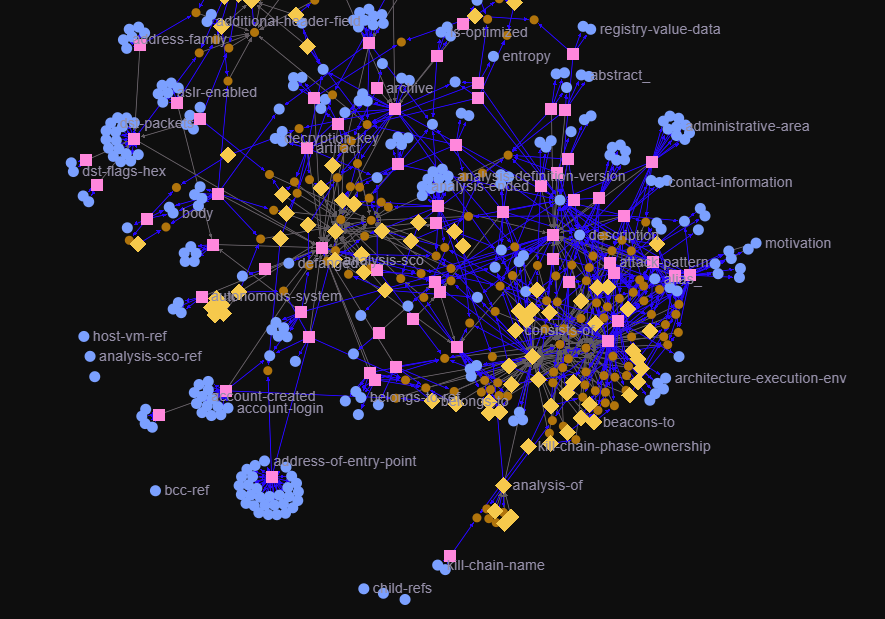
Understand threats as networks, not events.
TypeDB gives cybersecurity teams a smart database to model entities, relationships, and patterns, enabling faster, deeper detection and investigation.
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
match
$attack-pattern isa attack-pattern, has name like "T1078";
uses($attack-pattern, $campaign);
attributed-to($threat-actor, $campaign);
fetch {
"threat actor" : $threat-actor.name,
"campaign name": $campaign.name
};TypeDB is designed to find patterns in complex systems
Cyber threat intelligence depends on understanding how things connect. Systems, users, credentials, files, and behaviors form vast, shifting networks that can’t be flattened into rows or handled with ad-hoc joins.
TypeDB models entities, relationships, and functions as first-class citizens, letting you represent meaning directly in the data itself. Constraints and type safety are maintained at all times.
In CTI, these design decisions combine into something powerful: a system that doesn’t just store threat data, but understands it. With TypeDB, analysts can interrogate a model of the environment itself. This makes threat detection faster, investigations deeper, and the conclusions verifiable.
Structure and intent
Every entity and relationship has semantic definition, ensuring consistent meaning across sources.
Functions that scale
TypeDB functions can abstract away layers of logic, hence deriving new insights automatically, detecting hidden relationships and attack paths that would take manual correlation to find.
Safety by design
The schema enforces constraints and roles, guaranteeing data integrity even as your threat graph evolves.
Related articles
Unify your threat data
Bring all your intelligence sources into a single semantic model. Build models that incorporate data from SIEMs, MISP feeds, and internal telemetry all into TypeDB while preserving structure and meaning.
- Flexibly extend core entities: users, hosts, IPs, files, vulnerabilities, and incidents.
- Capture relationships such as communicates-with, hosts, authenticates-to, and targets.
- Keep structure enforced by schema, not convention.
Each new event enriches the graph, adding context for every future investigation. Over time, your knowledge base becomes a living map of your environment.
Result: Threat data becomes cumulative, contextual, and queryable across all sources.
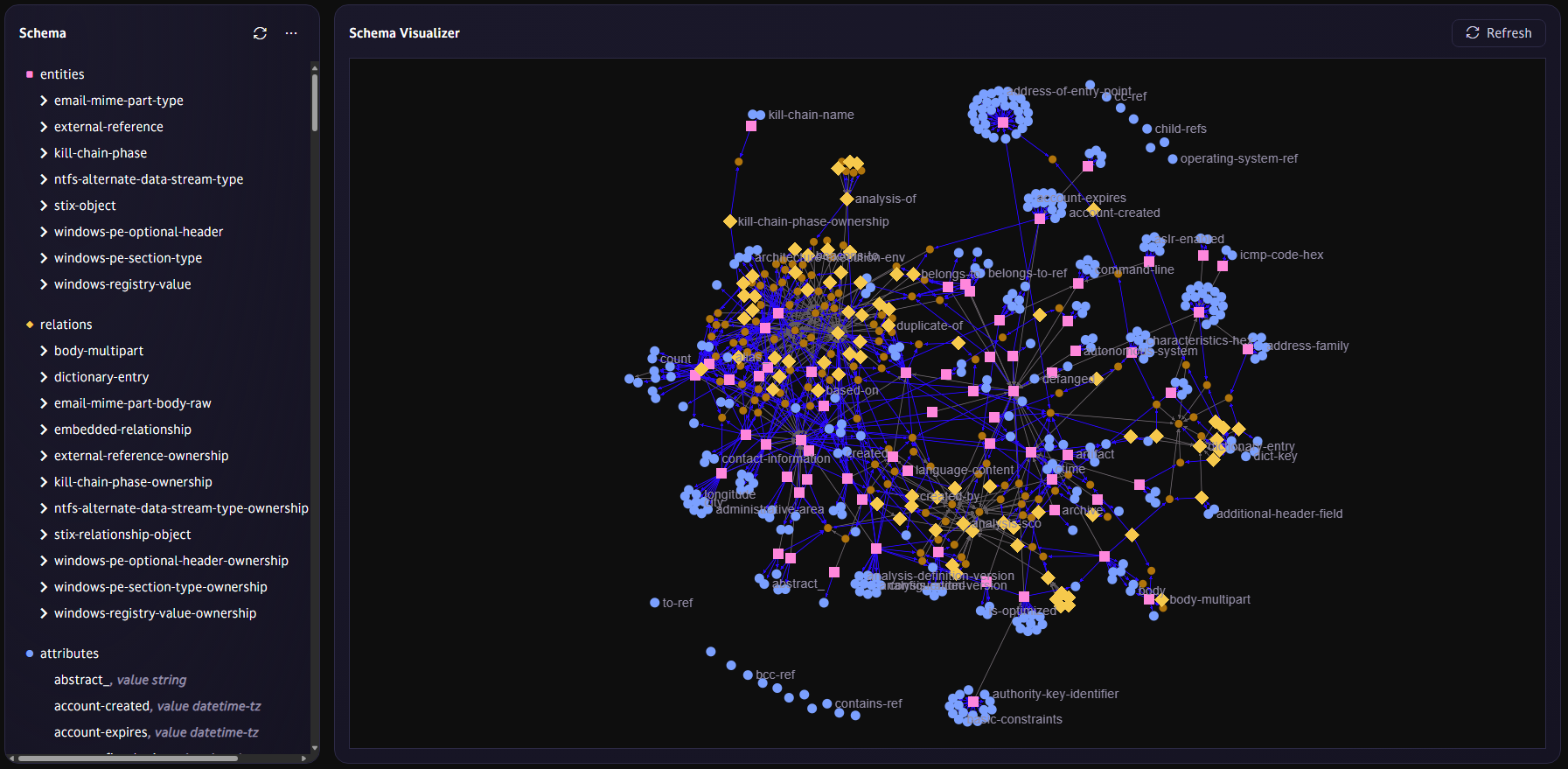
Build explainable, secure intelligence
TypeDB’s schema ensures that every query and inference follows logical, auditable structures.
No more opaque correlations or “ML says so” findings, your intelligence is transparent and defensible.
- Every response can be traced back to the source facts.
- Role-based access and audit trails protect sensitive data using TypeDB Enterprise.
- Works alongside your existing stack: Using TypeDB's client APIs, you can easily integrate model SIEMs, ML systems, and analytics platforms.
Result: An intelligence system your engineers and compliance teams can trust.
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
match
$campaign isa campaign, has name like "Salt Typhoon";
indicates($indicator, $campaign);
$indicator has confidence $confidence;
sort $confidence;
fetch {
"indicator": $indicator.name,
"description": $indicator.description
};Get started in minutes with CTI on TypeDB Cloud
You can explore TypeDB for Cyber Threat Intelligence today — no setup, no servers, no integration backlog. TypeDB Cloud comes with a preloaded CTI dataset and schema template implementing the open-source STIX 2.1 standard, so you can start exploring how TypeDB works in practice right away.
How it works
- Sign up to TypeDB Cloud.
- Boot up a free cluster with the CTI sample dataset preloaded. It includes a STIX schema with entities, indicators, and incidents modelled semantically.
- Run your first queries. Uncover relationships between users, hosts, IPs, and attack campaigns in seconds. In TypeDB Studio, using our new vibe querying capability, you can automatically turn natural language questions into queries!
- Modify the schema to reflect your own environment or data model when ready.
In under five minutes, you’ll have a running environment showing how TypeDB unifies threat data, reveals hidden connections, and powers real-time intelligence.